My son decided that he wanted to build a gaming PC for his 11th birthday earlier this month. It’s been years since I have done a PC build, but I was pretty sure I could remember/figure out how to attach pieces together into a functional PC.
We started the process with a shared (OneDrive) Word Doc. I wanted my son to do as much of the research as possible. He had a pretty good handle on all of the necessary components from endless gaming Youtubers explanations of their rigs. When he had to make a choice (AMD vs. Intel), he searched for opinions online with references to the software he likes to use. His target workloads included Minecraft, Unity Game Development, & Blender modeling.
My son did a first-pass at a materials list, including a 8th-gen Intel Core i5-8400 CPU, ASUS Radeon RX 560 video card, 16 GB of RAM, 1TB Hard Drive, Case, Motherboard, Power Supply and all the trimmings. I had him run through the wattages for all of his planned components to make sure that we were well in spec for the power supply.
The next step involved me putting the list through a “Dad lives by a budget” reality check. The Intel Core i5-8400 was trimmed back to an Intel Core i3-8300. The ASUS video card and Motherboard were swapped for slightly cheaper Gigabyte equivalents. The RAM was scaled back to just 8GB. I added a Bluetooth and Wifi adapter to the list for flexibility in setup/accessories, and also a copy of Window 10 Pro, so that he’d be able to use Remote Desktop to access the new machine from his much less powerful laptop.
The final Materials List looked like:
Case: DIYPC DIY-F2-O Black/Orange USB 3.0 Micro-ATX Mini Tower (Amazon Link)
Motherboard: GIGABYTE B360M D3H LGA 1151 (300 Series) Intel B360 (Amazon Link)
CPU: Intel BX80684I38300 65W Core i3 i3-8300 Processor (Amazon Link)
Memory: Patriot Signature 8GB (2x4GB) DDR4 2400 (PSD48G2400KH) (Amazon Link)
Video Adapter: Gigabyte Radeon RX 560 GAMING OC 4G REv2.0 (Amazon Link)
Hard Drive: Seagate 1TB FireCuda Gaming SSHD (ST1000DX002) (Amazon Link)
Power Supply: Thermaltake Smart RGB 500W 80+ (Amazon Link)
Operating System: Windows 10 Pro (Microsoft Link)
Extras: Plugable USB Bluetooth 4.0 Low Energy Micro Adapter (Amazon Link)
EDUP Wifi Adapter ac600Mbps Wireless Usb Adapter (Amazon Link)
Arctic Silver Thermal Compound AS5-3.5G (Amazon Link)
Everything was ordered and delivered before my son’s birthday, just waiting for him to dig in:
 Assembly was a breeze. The case had ample room for working. I provided a few pointers for making sure that the pre-installed stand-offs were positioned properly for the motherboard, and the ordering of install to make things easier. The new BGA socket for the processor was so much easier than the omg-did-i-bend-a-pin sockets of yesteryear.
Assembly was a breeze. The case had ample room for working. I provided a few pointers for making sure that the pre-installed stand-offs were positioned properly for the motherboard, and the ordering of install to make things easier. The new BGA socket for the processor was so much easier than the omg-did-i-bend-a-pin sockets of yesteryear.
We had a slight struggle with the Hard Drive because our initial attempt had the mounting frame even with the drive, which meant that the drive was not set in far enough that the case could close without pressing on the hard drive power cable. Correcting this was made harder by the fact that the hard drive was positioned to block the flexible part of the frame from bending to allow it to be removed from the case frame. This was remedied by some careful brute force.
Most every component and connector just went where they fit. My son handled all of the odds and ends with the motherboard’s included connector map. This case and motherboard actually matched pretty well for all the connectors. HD Audio header, all the remote USB ports, and each and every light and switch had a proper home. We even connected a tiny little speaker that was included in the motherboard package, “just in case” it was needed for POST beeps.
Once everything appeared to be in place, we connected the new box to a TV that we use as a monitor, and a keyboard and mouse that were birthday gifts from relatives, and hit the power.
The box hummed to life, orange LED lighting and fans spinning, and then a few second later everything cut off. Then on. Then off again. I hit the physical switch on the power supply so that we could get our bearings.
Next test we didn’t change anything, but took careful notice of all the fans. All spinning, so at least we weren’t cooking the CPU. Yet.
Next test, we unplugged pretty much everything non-essential on the motherboard, removed the video card and swapped the monitor over to the build-in HDMI connection and tried again. Same results.
Next test, one RAM module out: same. other RAM module out: same.
At this point I’m thinking that we’ve got a bad power supply, a bad motherboard, or a bad CPU. We disconnected the power supply, jumpered the green wire to ground, and applied power. It was nice to hear the power supply come to life and not power down after a few seconds. I didn’t check voltages, but I was pretty sure that we had a working power supply now. So basically at this point, I’m pretty certain that the motherboard is telling the power supply to cut off for some reason.
As I’m hooking the 24-pin power back to the Motherboard and trying to think of what to try next, I notice a lonely unpopulated 8-pin connector above the LGA1151 socket that looks to be another power connector. On closer inspection, it’s labeled “ATX_12V_2X4” and it most certainly is another power connector. When we were first hooking up the power supply, we’d checked all over the video card to see if it had and extra power socket (it doesn’t), but somehow missed this on on the motherboard. My son hooked up the extra power connector with one of the many available lines from the power supply and tried again… Success! We now had a booting computer! After seeing the BIOS menu come up, we powered down and my son set to work re-installing everything that had been removed in the name of troubleshooting.
After everything was hooked back up, the computer booted successfully again, and my son started the process of booting from a prepared USB to install Windows 10.
All in all, the build was a major success. My kids typically use cheap, modestly powered laptops for schoolwork and games, and this beast way outperforms all of them for the things my son cares about most (i.e. bragging about frames-per-second on Minecraft).

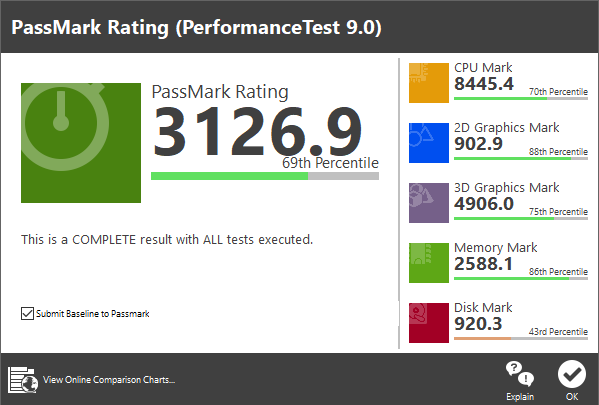
Passmark shows that our modest budget PC holds it’s own pretty well at 3126.9:


 Assembly was a breeze. The case had ample room for working. I provided a few pointers for making sure that the pre-installed stand-offs were positioned properly for the motherboard, and the ordering of install to make things easier. The new BGA socket for the processor was so much easier than the omg-did-i-bend-a-pin sockets of yesteryear.
Assembly was a breeze. The case had ample room for working. I provided a few pointers for making sure that the pre-installed stand-offs were positioned properly for the motherboard, and the ordering of install to make things easier. The new BGA socket for the processor was so much easier than the omg-did-i-bend-a-pin sockets of yesteryear.





